Blocks
Blocks
Cryptographic algorithms
A lot of security services such as confidentiality, integrity, authentication, and
non-repudiation can be provided by using
cryptographic algorithms.[1]- Confidentiality
Confidentiality serves
the purpose that information is not revealed to unauthorized entities.
Confidentiality is accomplished by transforming the understandable information
to a state that is unintelligible except by authorized entities. This
transformation mechanism is called encryption. The decryption of unintelligible
data is performed to restore it to its original state. Both symmetric and
asymmetric algorithms can provide encryption. Confidentiality is not only
important for data at rest but also for the network communication data.- Data Integrity
Integrity is the mechanism that assures that the data has not been altered in an unapproved way.
The integrity of data is maintained at the creation, transmission, and storage
phases. Alteration of data includes insertion, deletion, and substitution
breaches. Digital signatures and message authentication codes (MAC) are the
cryptographic mechanisms that can be used to notice both intentional &
accidental alterations.- Authentication
Source
and Integrity authentication. Source authentication assures the identity of the
entity that originally generated the information. Integrity authentication
validates that data has not been modified and the integrity of data is
protected.- Non-Repudiation
Non-repudiation is the guarantee that no one can deny a
transaction. The terminology of non-repudiation is frequently used for digital signatures
and email messages. When a data hashing algorithm is combined with
public/private keys, data origination authentication can be achieved. The
well-known technique of data origin authentication is using digital
certificates.
Cryptographic algorithms can be categorized into three
classes: Hash functions, Symmetric, and Asymmetric algorithms.
The proper approach to incorporate security services for
applications and protocols dealing with data security is the use of
cryptographic methods. A lot of public/open source and proprietary algorithms
are available. The document “NIST Special Publication 800-57 Part 1 Revision 4”
provides background information and establishes frameworks to support
appropriate decisions when selecting and using cryptographic mechanisms.[2]
The issue of
information security is extremely complex and at the same time complicated. The
main objective of the protection measures in a system is the elimination of the
possibilities of accidental or willful destruction of the information, as well
as of their unauthorized consultation. In the case of a computer system, the
problem becomes even more complicated when the data needs to be protected but
at the same time made available to the users.
Prevention
objectives can be achieved by encrypting information, an effective solution
when storing or transmitting data is done through unsafe environments.
Detection objectives are achieved if specific protocols are used, in
conjunction with cryptographic methods, which ensure the exchange of messages
between the entities of the respective computing system.
The encryption
gives protection to the information transmitted for the channels being listened
to or intercepted. For this purpose, the transmitter chooses an encryption
algorithm and a key, which it communicates to the receiver by secure means, for
example, by post or courier. Modern cryptography protects data transmitted over
high-speed lines and stored in computers.
Cryptography pursues two main
objectives:
- protection or confidentiality
(preventing unauthorized disclosure of information transmitted or stored);
- authenticity or integrity (preventing
unauthorized data changes) protected information.
NBS
(National Bureau of Standards - US) has published the requirements for the
encryption algorithm standard, which refers to:- must
provide a high level of security;
- must
be fully public, with complete specifications and easy to understand;
- the
security of the algorithm should be fully concentrated in the key strength and
not in the algorithm itself;
- must
be available to all users;
- must
be flexible, it can be adapted to different types of applications;
- the
implementation of the algorithm in electronic devices should be cheap;
- must
be efficient;
- provide
for the possibility of validating the algorithm;
- the
algorithm and the devices used by it can be exported.
A cryptographic system has the following
components [2]:
- clear text message space, {M};
- message space in encrypted text,
{C};
- keyspace, {K};
- family of encryption
transformations, 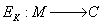 ; where
; where 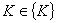
- family of decryption
transformations, 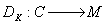 ; where
; where 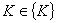
Each encryption / decryption transformation
is defined by an encryption algorithm respectively decryption.
In the specialized literature are used:- symmetric
method
Within
these methods, the basic feature is to ensure the secretion of the coding key,
on the one hand, and the uniqueness of the coding/decoding key, on the other.
In other words, the encryption key is the same for decoding the message, ie:
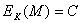 the encryption
operation
the encryption
operation
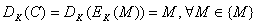 the decryption
operation
the decryption
operation
in which the same key K is used. Function E
represents the encryption operation (Encode) and D the decryption operation (Decode).
With these methods, data protection and
authentication can be ensured.- asymmetric methods
The concept of asymmetric cryptosystem was
introduced by Diffie and Hellman [3]
The
proposed encryption method consists in the use of the two processes, of coding
and decoding, of two keys for the specific operation. This method is also
called public-key encryption.
In these
cryptosystems, every user A has a public encryption transformation and a secret
decryption transformation, which cannot be obtained from the public encryption
transformation, as follows:
 the encryption
operation
the encryption
operation
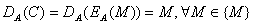 the decryption
operation
the decryption
operation
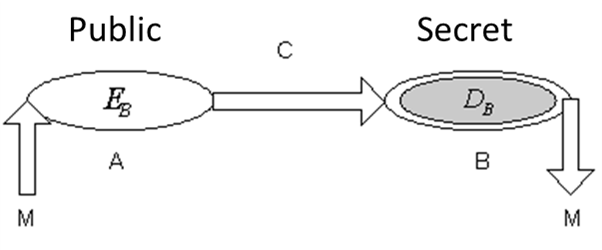
The mechanism is shown in figure 1
|
|
|
|
|
Figure 1. The asymmetric mechanism |
With these methods, data protection, and authentication can be ensured, according to the following schemes:
Either two users, A and B, who perform a coded message exchange, user A sends a coded message to user B, as follows:
- A will encode the message using the public key of user B;
- B will decode the message transmitted by user A, using his secret key.
1. For the protection of information the coding scheme is:
A: encryption:
B: decryption:
2. To authenticate the information the schema is:
A: sign information:
B: verify signature:
In this case, the confidentiality of the respective information cannot be guaranteed.
3. For the protection and authentication of information the scheme is:
A: encryption:
B: decryption:
[1] https://www.cryptomathic.com/news-events/blog/differences-between-hash-functions-symmetric-asymmetric-algorithms
[2] https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-57pt1r4.pdf
Last modified: Thursday, 8 July 2021, 9:39 AM