 Blocks
Blocks
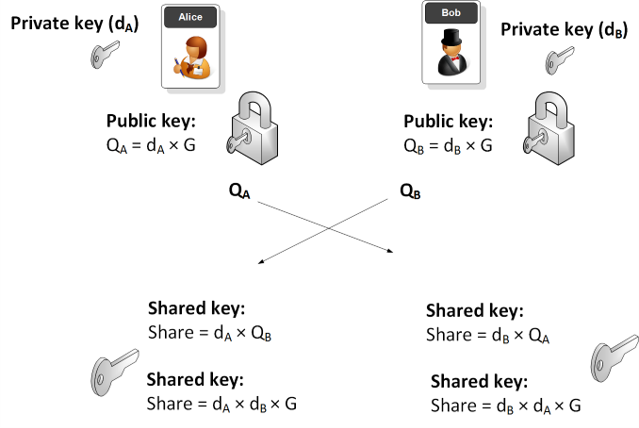
Digital Signatures
Digital signatures, like handwritten signatures, are unique to each signer. Digital signature solution providers follow a specific protocol, called PKI.
PKI requires the provider to use a mathematical algorithm to generate two long numbers, called keys. One key is public, and one key is private.
When a signer electronically signs a document, the signature is created using the signer’s private key, which is always securely kept by the signer. The mathematical algorithm acts as a cipher, creating data matching the signed document, called a hash, and encrypting that data. The resulting encrypted data is the digital signature. The signature is also marked with the time that the document was signed. If the document changes after signing, the digital signature is invalidated.
As an example, Alice signs an agreement to sell a timeshare using her private key. Bob receives the document. Bob also receives a copy of Alice’s public key. If the public key can’t decrypt the signature (via the cipher from which the keys were created), it means the signature isn’t Alice’s or has been changed since it was signed. The signature is then considered invalid.
Practice:
1. Open https://andersbrownworth.com/blockchain/public-private-keys/keys
2. Use the following keys:
Use the same algorithm to sign blockchain transactions.
PKI requires the provider to use a mathematical algorithm to generate two long numbers, called keys. One key is public, and one key is private.
When a signer electronically signs a document, the signature is created using the signer’s private key, which is always securely kept by the signer. The mathematical algorithm acts as a cipher, creating data matching the signed document, called a hash, and encrypting that data. The resulting encrypted data is the digital signature. The signature is also marked with the time that the document was signed. If the document changes after signing, the digital signature is invalidated.
As an example, Alice signs an agreement to sell a timeshare using her private key. Bob receives the document. Bob also receives a copy of Alice’s public key. If the public key can’t decrypt the signature (via the cipher from which the keys were created), it means the signature isn’t Alice’s or has been changed since it was signed. The signature is then considered invalid.

Practice:
1. Open https://andersbrownworth.com/blockchain/public-private-keys/keys
2. Use the following keys:
Private key:
18073215979049372419631649803864656504462095235754455718807233716436644998780
Public key:
04e411a5becfdbfacbd19761b95e05a90a4b4f554f15b74d8f4494178ef02034b3a7bceb42e340c55
6d2b60b1602eb2c53713866f3209732beb3566db36b9bd0d5
3. Verify the signature of this message:Message: Hello
Signature:
13045022100dbe9d22e4ec9081539a5831c860db4773bbb1ac9db7f947b5dc710457493bf5f0220
16d9ebb58b694112a5ad103be8b06e038f3586eaa63374c90fe57daaa828fbca
Use the same algorithm to sign blockchain transactions.
Last modified: Friday, 21 May 2021, 7:51 PM